macOS + Safari certificate weirdness
This isn’t directly a Let’s Encrypt issue, but I’m hoping this audience can help me resolve it as it’s obviously deeply related to SSL certificates. (If this is deemed too off-topic, please accept my apologies and let me know.)
On macOS (10.14.6), using Safari (13.1), Safari is telling me that it “can’t establish a secure connection to the server”. But only sometimes:
- The majority of sites work fine.
- It works fine after a reboot.
- Last time it went 27 hours after the reboot before re-occurring. ¯\_(ツ)_/¯
It’s weirder than that:
- OmniFocus, which establishes an SSL connection to https://sync3.omnigroup.com , also fails.
- Plenty of other sync services on my Mac do not fail. OF must be using the system certificates?
- Some sites which use the Let’s Encrypt Authority X3 certificate keep working (e.g. https://coruscade.com ).
- Other sites which use the same certificate chain fail (e.g. https://bum-man.com.au ).
- That last site is actually hosted at https://bumman2020.netlify.com . When accessed via that URL, the certificate is DigiCert SHA2 Secure Server CA and works A-OK.
- Firefox always works. So how does its certificate behaviour differ from Safari? Does it manage its own, and not use the system keychain?
- Brave fails but in a really weird way. It tells me that the cert is invalid ( NET::ERR_CERT_INVALID ) but when I inspect the certificates they’re all valid! Here’s an example of that, using another certificate that fails. ( https://theage.com.au is a large newspaper – this site works fine in Firefox.)

- When this issue occurs, it’s always the same certificates that fail. Repeatable, predictable.
- I have re-created my keychain. Made no difference – I assume that just deleted my personal stuff but didn’t touch the system root certificates?
I have a question open on StackExchange which has some more detail. This is driving me bananas.
Please someone here tell me how macOS certificate management works, and help me fix this. Thank you.
Yes, I think Firefox uses its own root store unless you configure it not to.
I don't have a solution for you other than to tell you that my sister experienced a similar thing on macOS some weeks ago. Except hers also had problems with some certificates from Amazon CA, until she rebooted her laptop.
e: One idea - on that screenshot, you are showing that the leaf certificate is valid. If you select the intermediate, or the root, do they also have the same "This certificate is valid" text?
Thanks, I’ll go digging around in Firefox and see if I can come up with anything interesting.
Yeah, Brave reports all 3 certificates in that screenshot as valid. Told you this was weird!
Stranger still: if I open a private window in Safari and browse to one of the broken sites, Safari warns me that “this connection is not private” and gives me the chance to “visit this website” as long as I authenticate to confirm that it is safe to do so.
When in a non-private window, I am not given this option. It’s just a flat-out “can’t establish a secure connection”.
If you're referring to your bumman site, it'd be because it's setup with an HSTS header . Browsers will omit the option to bypass the warning screen for HSTS-protected sites (that it's seen before, or are in the HSTS preload list).
When you browse the site in private mode, the HSTS cache isn't used, so the browser lets you through.
Don't think it explains your issue, though.
This recent thread is similar:
In that thread, the issue seemed to be that macOS didn't recognize a newer Certificate Transparency log that should have been supported since early December.
The OP said yesterday that it was fixed after installing a recent update.
If it works for OP after a reboot, it might be what made it “work” for me after applying the the update (since it rebooted). I’ll have to wait and see, I guess.
OP, you say all updates are installed, does that also imply the 002 security update from end of March?
OK, the issue is back on my Mac now, so it seems we have the same issue, and that it’s solved temporarily by rebooting. The latest security update ( https://support.apple.com/en-gb/HT211100 ) did not solve it.
@jen729w , are you by any chance using Little Snitch?
@jockek Sibling! You have it too. I’m not alone.
I do use Little Snitch, yes. Always have, config hasn’t changed in however long. These servers ping just fine and I’ve tried this with the network filter off, no change.
I recall a recent security update, yes. They pop up I do them as soon as I see them.
Have you and @jockek tried to see if those websites work in safe mode? (e.g. disabled all extensions and other potential softwares). Other networks? Have you submit any reports to Apple Support?
The problem with safe mode is that the issue is fine immediately after a reboot. I’d need to operate in safe mode for ~24h until it occurs, which I can’t afford to do. This is my main work machine.
I have tried other networks, yes. The network is not the issue.
This topic was automatically closed 30 days after the last reply. New replies are no longer allowed.
- Opportunities
- Free Speech
- Creativity and Innovation
- Transparency
- International
- Deeplinks Blog
- Press Releases
- Legal Cases
- Whitepapers
- Annual Reports
- Action Center
- Electronic Frontier Alliance
- Privacy Badger
- Surveillance Self-Defense
- Atlas of Surveillance
- Cover Your Tracks
- Crocodile Hunter
- Donate to EFF
- Giving Societies
- Other Ways to Give
- Membership FAQ
Search form
- Copyright (CC BY)
- Privacy Policy

Encrypting the Web

The web has largely switched from non-secure HTTP to the more secure HTTPS protocol. All web servers use one of these two protocols to get web pages from the server to your browser. HTTP has serious problems that make it vulnerable to eavesdropping and content hijacking. HTTPS fixes most of these problems. That's why EFF, and many like-minded supporters, have been pushing for web sites to adopt HTTPS by default. As of 2021, about 90% of all web page visits use HTTPS. This is a big win for encryption and security for everyone. It’s easier than ever to implement HTTPS by default, and we're providing the tools to do it.
For many years, web site owners chose to only implement HTTPS for a small number of pages, like those that accepted passwords or credit card numbers. However, over the last ten years, the Internet security community has come to realize that all web pages need protection. Pages served over HTTP are vulnerable to eavesdropping, content injection, and cookie stealing, which can be used to take over your online accounts.
Content injection is when someone adds data or code to your communications with an HTTP web page. For example, it's how GCHQ and NSA took over a Belgian ISP's computers . Content injection is also how China took down GitHub with a massive DDoS attack, dubbed "The Great Cannon" . Content injection is also becoming popular with ISPs. Verizon injected tracking headers into every request made by their customers. And Comcast injects pop-ups into sites where they don't belong . All of these attacks can be stopped by HTTPS, provided it is implemented and made default on enough sites.
What you can do as an individual
You can only use HTTPS on websites that support it, and there are still sites that don't send visitors to the HTTPS version by default. You can now force HTTPS by default in Chrome, Firefox, and Microsoft Edge.
Settings > Privacy & Security > Scroll to Bottom > En able HTTPS-Only Mode
enable_httpsonly1.gif
Settings > Privacy and security > Security > Scroll to bottom > Toggle “Always use secure connections”
This f eature is also under th e flag chrome://flags/#https-only-mode-setting .
chrome_https_only1.gif
This is still considered an “experimental feature” in Edge , but is available in Edge 92.
- Visit edge://flags/#edge-automatic-https and enable Automatic HTTPS
Hit the “Restart” button that appears to restart Microsoft Edge.
edge_https_only.gif
EFF’s browser extension, HTTPS Everywhere will retire at the end of 2022, because default HTTPS is now available on most websites without the extension. We see this as a great victory. HTTPS Everywhere was always meant to be a stopgap solution until more of the web was automatically encrypted.

What you can do as a web site owner
We're encouraging everyone who runs a web site to offer HTTPS and redirect visitors to HTTPS by default. Offering HTTPS has gotten a lot cheaper in the last 10 years.r. In fact, offering HTTPS makes it possible for sites to implement the modern HTTP/2 standard, which can dramatically speed up web browsing relative to HTTP . This also future proofs for even more up to date protocols that promise even more performance gains like HTTP/3-QUIC .
Offering HTTPS requires getting a certificate from a certificate authority. It used to be expensive and complicated to get a certificate, but since 2016, a new certificate authority, Let's Encrypt , offers free certificates to the public using an API that enables easy automation. Let's Encrypt is a joint project of EFF , Mozilla , and many other sponsors.

If you manage your web site entirely through a web interface, the easiest approach is for your hosting provider to integrate Let's Encrypt support as a setting you can turn on. Many hosting providers already support Let's Encrypt, and many more add support all the time.
If you have shell access on your hosting provider, you can use Certbot , a tool developed by EFF. Certbot can get you a free certificate from Let's Encrypt. It can also automatically configure your Apache or Nginx server to correctly use that certificate.

What you can do as a hosting provider
We encourage all hosting providers and CDNs to offer HTTPS by default for their customers, at no additional cost versus their HTTP services. Many already have, like Cloudflare , OVH , WordPress.com , and SquareSpace . The Let's Encrypt integration guide has additional details on how to best implement HTTPS by default. We continue to celebrate free, automatic HTTPS being the industry standard for web hosting.

EFF Related Content: Encrypting the Web

Should Caddy and Traefik Replace Certbot?
Can free and open source software projects like Caddy and Traefik eventually replace EFF’s Certbot ? Although Certbot continues to be developed, we think tools like these help offer a promising path forward in the further development of a secure and encrypted web. For some users, tools like...
- Read more about Should Caddy and Traefik Replace Certbot?

Privacy Isn't Dead. Far From It.
Welcome! The fact that you’re reading this means that you probably care deeply about the issue of privacy, which warms our hearts. Unfortunately, even though you care about privacy, or perhaps because you care so much about it, you may feel that there's not much you (or anyone) can really...
- Read more about Privacy Isn't Dead. Far From It.
The Last Mile of Encrypting the Web: 2023 Year in Review
At the start of 2023, we sunsetted the HTTPS Everywhere web extension. It encrypted browser communications with websites and made sure users benefited from the protection of HTTPS wherever possible. HTTPS Everywhere ended because all major browsers now offer the functionality to make HTTPS the default. This is due to...
- Read more about The Last Mile of Encrypting the Web: 2023 Year in Review

EFF Launches the Tor University Challenge
SAN FRANCISCO—Electronic Frontier Foundation (EFF) on Tuesday launched the Tor University Challenge , a campaign urging higher education institutions to support free, anonymous speech by running a Tor network relay. Universities answering this call to defend private access to an uncensored web will receive prizes while helping...
- Read more about EFF Launches the Tor University Challenge

Celebrating Ten Years of Encrypting the Web with Let’s Encrypt
- Read more about Celebrating Ten Years of Encrypting the Web with Let’s Encrypt
Back to top
Follow EFF:
Check out our 4-star rating on Charity Navigator .
- Internships
- Diversity & Inclusion
- Creativity & Innovation
- EFFector Newsletter
- Press Contact
- Join or Renew Membership Online
- One-Time Donation Online
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
Website suddenly doesn't open in Safari and iOS devices
I have this website that was working fine until recently. Now users are reporting that it's not opening in their iphones and ipads.
Doesn't matter what browser you try on iOS, it just won't work. Also it doesn't open in Safari when browsed on a Mac machine. Other browsers work fine though (Mac OSX only, not iOS).
Here is the server configuration:
DigitalOcean + Ubuntu 18.04 + Nginx + PHP 7.3 (Laravel) + Let's Encrypt SSL + HTTP2 activated
Before I explain further, I wanna mention that using the same type of configuration as above, I have another server which is running fine and is accessible from all devices. They are almost identical (in terms of config and setup) apart from domain name and ip address obviously.
Another tiny extra info which I think is worth mentioning, is that my users are located in Iran.
Here is a list of things that I've checked:
- The domain is accessible using ping command from iOS and Mac.
- The IP address itself is also accessible, and it can be used to browse the site, it will just show a "invalid ssl certificate" warning.
- The DNS that were used for the domain are all ping-able from iOS and Mac.
- If a VPN connection is used, the site can be accessed. Which is really weird because everything is technically reachable, the domain, the ip and the dns.
- Aside from using a VPN, the site can also be accessible if SSL is completely turned off/disabled.
- Other public websites that are using Let's Encrypt SSL are all accessible. So it can't be a Let's Encrypt issue.
Here is what I've tried so far:
- Tons of googling. I've even came across with a user with same type of issue on here and here and here
- I've tried disabling HTTP2.
- I've double checked my firewall settings, and even tried disabling it.
- I've tried disabling GZIP.
- I did a ssl test on ssllabs.com and it shows no problem and it's identical to my working server.
- Tried using keepalive_disable "safari" in nginx config
- I've tried swapping ssl_protocols values, like only accepting TLSv1.3 or dropping TLSv1.0
- Tried using ssl_session_cache
- Tried changing ssl_ecdh_curve to auto and secp384r1
- Tried changing ssl_ciphers to HIGH:!aNULL:!MD5; and EECDH+CHACHA20:EECDH+AES128:RSA+AES128:EECDH+AES256:RSA+AES256:EECDH+3DES:RSA+3DES:!MD5;
- Tried changing ssl_session_tickets to on and off
- Tried using Strict-Transport-Security
- Tried commenting /etc/letsencrypt/options-ssl-nginx.conf which is used by certbot
- Tried different HTTP to HTTPS redirect settings
- I made sure to use private tab when testing to make sure i'm not looking at a sort of faulty cached attempt to reach the site.
- I did service nginx reload & restart everytime I made a change to config files.
- I did lots of sudo reboots to make sure it's not a simple reboot issue.
As a final resort, I even went through the trouble of reinstalling the OS from scratch and setting up the server again. Still Doesn't work. And no I didn't copy my config files, I did every command manually and modified config files carefully to make sure I don't bring any problems from previous setup. This also means I did a fresh SSL request from Let's Encrypt (using cerbot). Although I don't know if they generate a new one or the send you the one from last time.
EDIT 1 : I want to throw a random thought in here. I really don't know about advanced networking but maybe something from Iran censorship firewalls is meddling with the SSL connection and that causes Apple devices to fail establishing the connection. I heard Apple is strict in it's own way and requires a specific SSL connection unlike chrome and firefox. those 2 might ignore a slight error but Apple devices don't.
EDIT 2 : I checked the Safari while Wireshark is tapping. It seems only few packets gets exchanged only no matter what I do. Also it seems Safari is using TLSv1.0 even though I've disabled it in nginx config. I really don't know how completely turn it off so Safari won't even try to use it to communicate with the server.
EDIT 3 : I tried using a different SSL (using comodo's 3 month free ssl trial program) and the issue is still there... I read some people saying they resolved some similar issues after changing their SSL. I don't know why it's not working for me.
EDIT 4 : I decided to change DNS servers of the domain to see if it's a DNS issue. I don't know why and how but after I changed them, Safari could load the site briefly. But after sometime it stopped working again.
EDIT 5 : No luck with disabling external script codes in my site, like google analytics ( because their service is kinda blocked for Iranians ). Again, I read people reports implying that some fixed their issue by disabling external scripts.
EDIT 6 : I'm starting to believe this is not a networking or server config issue on my part. It really looks like a 3rd party interfering with the request. I don't know about Apple and how it handles networking, but I think Apple connection/packeting negotiations is causing some sort of red flag so to speak and that makes Iranian censorship/firewall to drop the client connection.
EDIT 7 : I even changed the server's datacenter, with a fresh new ip address. the issue still exists :(
EDIT 8 : This is the /var/log/nginx/error.log output when it's set to debug . It shows these lines when I initiate a request from a Safari client.

I did try to disable php fpm to make sure it's not a php bottleneck issue. Also I tried to tweak some random parameters, like bumping net.core.somaxconn to 1024 or increasing backlog in php fpm config files. Also when I watch the system using htop everythink looks normal, no cpu usage spikes and no specific process jumping to top of the list.
EDIT 9 : I swapped Nginx to Apache2 to check if it's a webserver issue. Well, it wasn't.
- lets-encrypt
- In HTTP it work? – yagmoth555 ♦ Jul 20, 2019 at 11:11
- @yagmoth555 yes it works without any issues if I disable ssl. – Hassan Jul 20, 2019 at 14:40
- "...users are reporting that it's not opening..." Ok but is it all working for you? – Rob Jul 20, 2019 at 16:19
- @Rob No it's not working for anyone who's trying to accessing from Iran, including me. I stated it that way meaning that is how I got informed. – Hassan Jul 20, 2019 at 16:21
- 1 @Rob yes. and as I mentioned in the main post, using a VPN would solve the problem. I think something from Apple's devices is causing Iranian firewall/censorship devices to drop the connection. But it's probably a really rare case. Because all other sites and services work just fine. – Hassan Jul 20, 2019 at 16:29
4 Answers 4
Since you doubt the proxy in-between you and the website, can you bypass it by using the -L option in ssh? It will provide a secure tunnel between you and your website that cannot be altered by the proxy.
For example, execute this on your desktop: ssh -L 2222:127.0.0.1:443 [email protected]
Once this command has logged into your server, fire up the browser on the same desktop to https://127.0.0.1:2222
If you now see you site and its SSL certificate, everything is setup correctly - theres someone in the middle altering your SSL connection when you are not using the tunnel.
- I don't have any problem SSH'ing into the vps and yeah i know someone, or should i say, the government firewall is killing the apple devices requests for some reason. I know they're sensitive to encrypted data. But I really don't know why and how only apple devices are affected. they're triggering some sort of protocol or specific routing that the censorship hardwares don't like. I really wish I could fix this at user's level. This is so randomly only happening to my site. It used to work fine few weeks ago and now it's just getting picked up by the firewall. ofc I can disable SSL & keep going – Hassan Jul 25, 2019 at 20:21
- OpenSSL includes a client that you can test with. For example: openssl s_client -connect mywebsite.com:443 Does this connect? – Austin Dixon Jul 25, 2019 at 20:47
- It does connect. I did mention in my post that only the browsers are affected. command line connections work fine. – Hassan Jul 26, 2019 at 9:24
I found a temporary solution to my problem. I just moved the server to a different hosting/datacenter!
Update: Actually the problem reappeared again after few months... I really don't know what technical issue is causing the problem or how to fix it.
Update 2: I talked to an IT networking expert and they told me the issue actually relies in government firewall rules picking up on my domain name ( false/wrong censorship ) and it doesn't matter what webserver configuration or webhosting I use, it just keeps getting blocked by firewalls out of my reach.
- 1. did you check your firewall using the ufw?, 2. did you add the auto renewal of certbot certificate in your cron using '0 0,12 * * * root python -c 'import random; import time; time.sleep(random.random() * 3600)' && /usr/local/bin/certbot-auto renew -q" | sudo tee -a /etc/crontab > /dev/null' this comment? 3. get the ssl params settings from my answer stackoverflow.com/a/63750775/3462686 . 4. And also check the folder permission and chmod – Karthikeyan Ganesan Sep 5, 2020 at 5:41
It could just be the certificate, do you have SubjectAlternativeName properly set? Only using the SubjectName for the DNS name is deprecated. Do you use certificate pinning, OSCP stapling, HSTP, and other relatively new TLS settings? That might cause issues on regulated networks.
Some internet users need to use a proxy with SSL-inspection. Many corporate environments use products similar to IronPort or Bluecoat to detect covert channels and malware as part of their security policy. The way to do this originated from an article in the underground magazine Phrack 76. It boils down to a simple setup where each client has an additional CA root certificate of the proxy that it trusts, the proxy in turn re-initiates connections on behalf of each client, "opening the SSL" by MIT, countries like Iran and China monitor the internet at large. Due to this there is no PFS, and several things might fail that depend on the client checking the servers' crypto, because it is altered or ssl is even completely removed. If you don't care about it then you can downgrade your server certificate settings to "export quality" by removing mentioned options.
- I don't know about about "SubjectAlternativeName" but I tried Let's Encrypt SSL and as I mentioned later in my post in my 3rd edit, I swapped to Comodo's free 3month trial to check if it's a Let's Encrypt issue, and it wasn't. Also I tried every possible combination of ssl options like the ones you mentioned, OSCP stapling, HSTP, etc... – Hassan Jul 22, 2019 at 19:09
- The idea is to use a little SSL as possible, to allow SSL inspection. You tend to tighten it too much. – bbaassssiiee Jul 22, 2019 at 19:27
@austin-dixon's answer is on the right track. That test would have to be done from the same country the users are in, which may not be an option if you are not already in that country.
You may be able to at least validate the configuration by using the Qualys SSL test at https://www.ssllabs.com/ssltest/ . The letter score doesn't matter in this case, just scroll down to Handshake Simulation and see how the Apple devices are expected to perform under normal circumstances.
Either way that just confirms what you already suspect, that there's something in between those users and the site. There are not a lot of ways for a developer to get around that situation short of disabling HTTPS completely. It's possible the man in the middle requires some of the weaker cipher suites or lower TLS versions than the server is configured for, but I wouldn't know which ones to suggest in that case.
- You should have read the post and it's comments. I did state that I'm located in the problematic country at the moment. Also I did run a ssl test on ssllabs.com it shows no errors or problems. and the apple devices are looking fine under handshake simulation. And I did try to change the ciphers and the TLS version. It didn't help the situation. – Hassan Jul 26, 2019 at 9:31
- Did @austin-dixon's test work? You said SSH works but not whether browser traffic going through that SSH tunnel shows the problem behavior. – wrk2bike Jul 26, 2019 at 14:19
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged nginx ssl lets-encrypt ios safari ..
- The Overflow Blog
- Will antitrust suits benefit developers?
- Are long context windows the end of RAG?
- Featured on Meta
- New Focus Styles & Updated Styling for Button Groups
- Upcoming initiatives on Stack Overflow and across the Stack Exchange network
Hot Network Questions
- Is it possible to fill an arbitrarily large hex grid completely given these rules? #2
- Does a carbon fiber fuselage suffer wear from pressurization/depressurization?
- How many cacti can I plant here?
- Is it possible to have very different sea levels?
- What is the meaning of 8va combined with the bracket?
- Is there something in international law that you can't bomb the embassy of country X in country Y (to kill a HV target) if you're at war with both?
- Node in unwanted position using tikzpicture
- What were the most common software distribution formats for MacOS Classic?
- Temporarily replacing one pane of glass in a double-pane door
- How is this possible: a moon with A) large apparent size B) that spins C) spins in a 5:1 spin-orbit resonance?
- Does a direct flight emit more CO2 than a flight with a layover?
- Indesign, table: How to horizontally align text and object in table cell
- When was "Fast Trip" by James White Published?
- What does "Funnies" refer to?
- How to become a FIDE Candidate Master?
- Drawing a set partition
- Should I cut or detach a ground wire for a light fixture to remove it?
- Shower rod adhesive for tile
- If you have a group of levers, dials, knobs, buttons, &c, what do you call a specific 'snapshot' of the way they are set?
- Did Esau ever “break Jacob's yoke from his neck”? (Genesis 27:40)
- Nuclear attack followed by a ground invasion
- A barred crossword for today
- Behaviour of Functions in Sourced Scripts
- Find Text Between tabs

Safari's 'Not Secure' Warning for Websites with Let's Encrypt Certificates
Abstract: A website's certificate has been automatically renewed via Let's Encrypt, but Safari continues to display a 'not secure' warning.
Safari's Not Secure Warning for Websites Without Lets Encrypt Certificates
In recent years, web browsers have started to display a "Not Secure" warning for websites that do not have an SSL/TLS certificate installed. This is an effort to encourage website owners to secure their sites and protect their users' data. One such browser that displays this warning is Safari, which is the default browser on Apple devices. However, there is a free and automated solution to this problem: Lets Encrypt certificates.

What is a Lets Encrypt Certificate?
Lets Encrypt is a nonprofit Certificate Authority (CA) that provides free, automated, and open SSL/TLS certificates. These certificates are used to encrypt the connection between a user's web browser and the website they are visiting, ensuring that all data passed between the two is secure. Lets Encrypt certificates are trusted by all major web browsers, including Safari.
Why is Safari Displaying a "Not Secure" Warning?
Safari, like other web browsers, wants to ensure that its users are protected from potential security threats. One way it does this is by displaying a "Not Secure" warning for websites that do not have an SSL/TLS certificate installed. This warning is meant to alert users that the website they are visiting is not using a secure connection, and that their data may be at risk.
However, this warning can be misleading, as many websites without SSL/TLS certificates are not necessarily insecure. Instead, they simply have not yet implemented a certificate. This is where Lets Encrypt comes in.
How to Fix the "Not Secure" Warning with Lets Encrypt
To fix the "Not Secure" warning in Safari, website owners can install a Lets Encrypt certificate. This process is automated and can be done for free using a tool such as Certbot. Once the certificate is installed, the website will be able to establish a secure connection with the user's web browser, and the "Not Secure" warning will no longer be displayed.
Benefits of Using Lets Encrypt Certificates
There are several benefits to using Lets Encrypt certificates, including:
- They are free and automated, making it easy for website owners to secure their sites.
- They are trusted by all major web browsers, ensuring that users are protected.
- They help to improve a website's search engine ranking, as search engines favor sites that are secure.
- They help to build trust with users, as they see that the website takes their security seriously.
The "Not Secure" warning in Safari can be alarming for website owners and users alike. However, it is easily fixed by installing a Lets Encrypt certificate. This not only helps to secure the website, but also improves its search engine ranking and builds trust with users. With Lets Encrypt, securing a website has never been easier or more affordable.
- Lets Encrypt
- Why HTTPS Matters
Tags: : Safari Certificates Security
Latest news
- Making Modal Pop-ups Responsive: Bottom Right Desktop, Centered Mobile
- Centering Checkboxes in a Cell: A Solution
- Integrating Nut-Sdk Java Module into React Native for BLE Device Scanning
- Deploying Django App on Elastic Beanstalk: MySQL Client Issue
- Making Floating Elements Peek Over Border with Enough Space: A CSS and HTML Approach
- Creating a Custom Tokenizer using Hugging Face Tokenizers Library: Model Fit's Tokenizer
- Retrieving OUTPUT Values from a Table Variable using Dapper in SQL
- Resolving Expected Parameter Declarator Error in C Programming
- Solving LeetCode: Find the Single Unique Element using Array.FindIndex in C#
- Unable to Render Swagger-UI with OpenAPI Specification in PostgREST
- Speeding Up MYSQL Queries with Indexes: A MariaDB Example
- ResourceAccessException: Unable to Find Valid Certification Path for POST Request
- BBCode Parsing Issue Inside Spoiler Tag
- Connecting Python App to Keycloak Server using Keycloak Python Library
- Providing Type Hints for Python's Graph Traversal: Ensuring Expected Shapes
- Difficulty Getting Number Data: Incorrect ArchiveChat Model Results in Django
- Add, Delete, Modify Data with TortoiseORM: A Model Class Example using Cellery
- Debugging a System.StackOverflowException in Debug Mode
- Setting Cookies in Localhost Developing Environment with Next.js and Express.js
- Android Gradle Plugin Not Updating: Resolving Version Mismatches
- Resolving Issues with OAuth2.0 Access Tokens Not Working on Software Development Site
- Understanding IA-32 Mode and Unable to Read/Write Memory Above 4GB
- Error Setting NGHTTP2 Options in Laragon (Windows) with PHP 8.3.4
- Next.js App Router Project Not Autoupdating: Localhost Save Issue
- Fonts Not Loading in Elementor: A Solution for WOFF2 Format and Moment Change CSS
- Detecting Nearby NFC Tags for Android Device Transactions
- Flyout Menu Stop Working in Formaciones Section on iOS
- Resolving WhitelabelErrorPage in VueJs and SpringBoot
- Making X/Y Tables Accessible in Software Development: A Testing Approach
- Solving Spatie PDF Image Header Base64 Source Issue
- Setting Up Local Environment with Node.js Version Management on MacBook Pro
- Uncaught Error in PrestaShop: Call to Undefined Method Tools::jsonDecode()
- Troubleshooting Laravel Application: White Blank Screen in CPanel
- Understanding and Handling Undefined Behavior in C: An Uninitialized Variable Example
- Mocking Chrome Extension Runtime API for Jest Unit Tests: Handling new Messages
Safari User Guide
- Change your home page
- Import bookmarks, history and passwords
- Make Safari your default web browser
- Go to websites
- Find what you’re looking for
- Bookmark web pages that you want to revisit
- See your favourite websites
- Use tabs for web pages
- Pin frequently visited websites
- Play web videos
- Mute audio in tabs
- Pay with Apple Pay
- Autofill credit card info
- Autofill contact info
- Keep a Reading List
- Hide ads when reading articles
- Translate a web page
- Download items from the web
- Share or post web pages
- Add passes to Wallet
- Save part or all of a web page
- Print or create a PDF of a web page
- Customise a start page
- Customise the Safari window
- Customise settings per website
- Zoom in on web pages
- Get extensions
- Manage cookies and website data
- Block pop-ups
- Clear your browsing history
- Browse privately
- Autofill username and password info
- Prevent cross-site tracking
- View a Privacy Report
- Change Safari preferences
- Keyboard and other shortcuts
- Troubleshooting
Digital certificates and encrypted websites in Safari on Mac
A certificate, also known as a “digital certificate” or a “public key certificate”, is a file that helps keep web communications secure.
Certificates are issued by trusted organisations, such as VeriSign, Inc. or RSA Security, Inc. When you visit an encrypted website — for example, to do online banking — Safari checks if the site’s certificate is legitimate. If it’s not, Safari warns you.
An encrypted website and Safari work together to encrypt information you exchange with the site. The key used for the encryption is contained in the site’s security certificate. This protects your login information, credit card numbers, addresses and other secure data.
If you need to connect to a website that requires a personal certificate, you’re provided with a certificate and instructions for installing it. After it’s installed, you gain authenticated access to the website automatically. If you’re unable to access it, contact the website administrator.
Open Safari for me
Let's Encrypt R3 Intermediate Certificate Expiration (30 September 2021)
It has come to our attention that we're currently including, by default, in our HTTPS redirector and DNSimple app certificate installer, an intermediate SSL certificate for Let's Encrypt that will expire on September 30, 2021.
In this post, we'll explain the actions we're taking to address this, and caveats to be aware of regarding the intermediate certificate provided by Let's Encrypt as a replacement.
The Let's Encrypt R3 intermediate
Let's Encrypt adopts a common architecture for a certification authority based on root and intermediate certificates. The certificate authority owns one (or more) root certificates that are embedded root stores in the various browsers and operating systems. These certificates are not used directly for signining server certificates, to minimize security risks. Instead, these certificates are used to sign intermediate certificates that are used to sign server certificates. This approach helps segregate root certificates in highly secure offline facilities, removing the need from using them for live signing – a process that inheritely increases the risk of the certificate being compromised. Root certificates are highly valuable and very complicated to revoke/replace compared to intermediate certificates.
Since their inception, Let's Encrypt has adopted cross-signed root and intermediate certificates. This approach allowed Let's Encrypt to issue trusted certificates from the beginning using another certificate authority root (IdenTrust), while working to get their root certificates accepted by the various root stores.
On November 6, 2020, Let's Encrypt announced their intention to switch away from cross-signing to rely solely on their own root certificates. They altered the plan soon after when they realized some incompatibilities with certain older devices – in particular Android devices.
In a follow-up announcement on 21 December 2020, they announced their revised plan for Android Compatibility . This plan included the use of additional cross-signing on their root certificates, and they postponed the transition from the cross-signed R3 intermediate to their own R3 intermediate.
The transition was completed on May 2021 . At this time, Let's Encrypt switched their default intermediate chain from using the certificate R3 (Cross-signed by IdenTrust) to the certificate R3 (Signed by ISRG Root X1) .
This is the current Let's Encrypt Hierarchy as of August 2021.
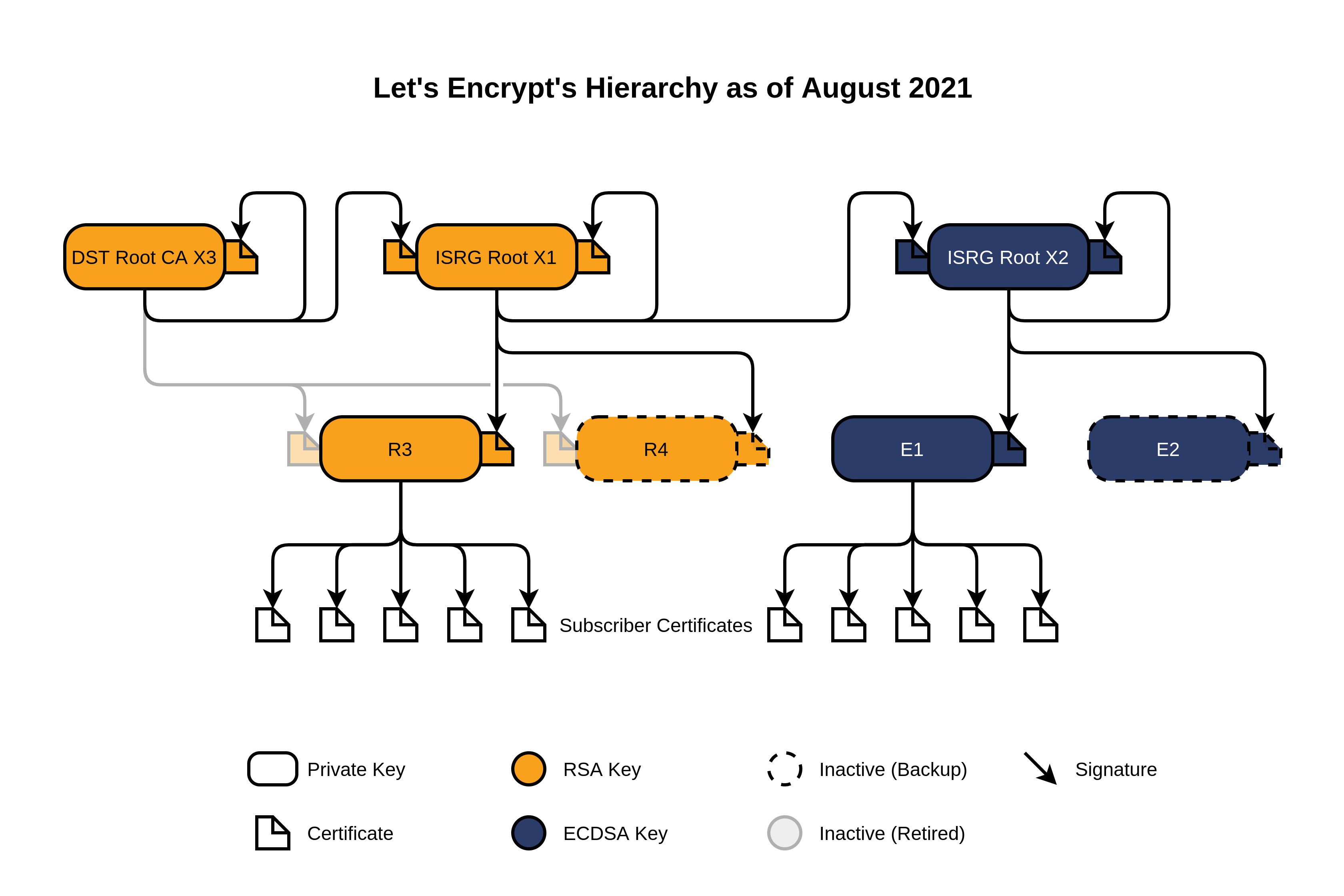
The former certificate R3 (Cross-signed by IdenTrust) has since officially been flagged as retired by Let's Encrypt. At DNSimple, we continued to include this certificate in the default intermediate chain we serve from the HTTPS redirector and our DNSimple app certificate installer.
We planned to verify and switch the chain in the upcoming weeks, but it has taken longer than expected. Unfortunately, the retired certificate will expire in four days, on 30 September 2021. For this reason, we're now taking immediate action as described below.
What we did
Updated the https redirector chain.
As of 28 September 2021 10:00 UTC, the HTTPS redirector has been updated to use the new R3 certificate.
Updated the DNSimple-app installer chain
As of 28 September 2021 10:00 UTC, the certificate installation wizard you can access from the dowload certificate page in the DNSimple app has updated to use the new R3 certificate.
What you need to do
If you're using Let's Encrypt certificates generated via DNSimple in our HTTPS redirector, you don't need to make any changes. Effective immediately, new HTTPS handshakes will use the non-expiring certificate.
If you're using Let's Encrypt certificates generated via DNSimple in your site, make sure to promptly replace the intermediate chain to use the non-expired intermediate certificate, as outlined below.
Replacing the retired R3 intermediate certificate
- Use this tool to verify if your site is using the retired R3 intermediate certificate.
- If confirmed, follow the instructions below to replace the certificate.
- You don't need to request a new certificate, or a reissue – just replace the intermediate certificate bundle.
- If you installed the certificate from the site, follow the same process to install it again . Download the certificate along with the updated bundle, and install it on your server or in the service like you would normally do on renewal every 90 days.
- If you installed the certificate via API , you likely have a process to download and replace a certificate on every renewal. Run your integration again to pull the updated version of the bundle, and replace it on your servers.
- Ship the changes, and confirm the fix by running the tool again.
What you need to know
As explained in the DST Root CA X3 Expiration (September 2021) page, there are some caveats when switching to this new chain.
On September 30 2021, there will be a small change in how older browsers and devices trust Let's Encrypt certificates. If you run a typical website, you won't notice a difference - the vast majority of your visitors will still accept your Let's Encrypt certificate. If you provide an API or have to support IoT devices, you might have to pay a little more attention to the change.
If you actively use a Let's Encrypt certificate for one of those two use cases (API provider and/or IoT devices), we strongly encourage reading the article above and following the Let's Encrypt recommendations to be prepared for the switch.
What we learned and future improvements
At DNSimple, we support two different certificate authorities: Let's Encrypt and Sectigo.
The last intermediate/root certificate change involving Sectigo resulted in more issues than expected. For this reason, we've taken additional steps to proactively notify all customers with an active Let's Encrypt certificate.
- There is a status page to track the progress of the update at DNSimple .
- This blog post will go live to document the issue and provide instructions.
- We'll notify all customers with an active Let's Encrypt certificate via email.
We're also rolling out some changes to automate the process of switching Let's Encrypt intermediate chain using the default bundle provided by Let's Encrypt ACME protocol. We've been hesitant to implement this automation to avoid altering the chain without proper vetting and notification. However, this approach will better mimic the ACME protocol experience and result in a better user experience for our customers.
If you have any questions, please contact support – we're always here to help.
Share on Twitter and Facebook
Simone Carletti
Italian software developer, a PADI scuba instructor and a former professional sommelier. I make awesome code and troll Anthony for fun and profit.
We think domain management should be easy. That's why we continue building DNSimple.

4.3 out of 5 stars.
Based on Trustpilot.com and G2.com reviews.
Introducing Notes for DNS Records
New Record Notes allow you to record why you made DNS zone changes.
Debugging DNS
In this post we share some tips and tools you can use to troubleshoot DNS issues on your own like a pro.
Elapsed time with Ruby, the right way
Elapsed time calculations based on Time.now are wrong. Learn why they are wrong and how to fix them.
Safari gets new encryption option for network privacy on iPhones, Macs
Apple's approach lets browsers and other apps, too, use encrypted DNS technology on the company's devices.

- Shankland covered the tech industry for more than 25 years and was a science writer for five years before that. He has deep expertise in microprocessors, digital photography, computer hardware and software, internet standards, web technology, and more.
Apple's Safari will take advantage later this year of new encryption technology that protects an important type of network communication called DNS. It's part of a broader movement to build privacy into internet technology like email and the web that initially sent sensitive data unprotected.
DNS, short for Domain Name System , looks up the numeric internet addresses needed to communicate with online sites we know by human-readable names like cnet.com or wikipedia.org. Loading a website, checking email and many other online activities perform many DNS lookups, but typically they're not protected with encryption.
Chrome and Firefox add that protection with a standard called DOH, or "DNS over HTTPS." Apple is embracing the same technology but is enabling it with the operating system, not the browser. And Apple also is offering a related encryption approach called DOT, which uses DNS over TLS, the encryption standard underlying the HTTPS technology for website security.
With iOS 14 , iPadOS 14 and MacOS Big Sur arriving later this year, though, Apple will let you add that protection to Safari , too, the company announced this week at its WWDC conference for programmers . Instead of building the protection directly into the browser, though, it's letting you install an app from a company like Cloudflare or Comcast that offers DOH support.
Apple's endorsement of DOH and DOT is an important moment for encrypted DNS. It's hard to retrofit privacy protections to decades-old technologies like DNS that are deeply embedded in the internet, but the shift to encrypted DNS is now well underway . On Thursday, Mozilla also broadened its support with a partnership to let Comcast handle Firefox DOH queries in accordance with Mozilla privacy requirements.
Privacy is a top priority for many tech players right now, and a key part of that push is encryption technology that scrambles data so it's impenetrable to those without the digital keys to decode it. Apple Chief Executive Tim Cook is arguably the most vocal privacy proponent in the tech world, and in the opening speech at WWDC , software chief Craig Federighi said, "At Apple, we believe privacy is a fundamental human right ."
Browsers and passwords
- How to install the iOS 14, iPadOS 14 developer betas
- Find out if iOS 14 will work on your iPhone. Here's the complete list
- MacOS Big Sur: Check out these 5 new features
- Apple gives Macs a brain transplant with new Arm chips starting this year
Not everyone likes encryption, though, as evidenced by proposed legislation like the Lawful Access to Encrypted Data Act and the Eliminating Abusive and Rampant Neglect of Interactive Technologies Act . Both proposals push to make it possible for authorities to get access to encryption keys from tech companies that today often don't have them.
DOH blocks snooping and tampering
Without encrypted DNS, "other devices on the network cannot only see what names you're looking up, but they can even interfere with the answers," said Tommy Pauly , an Apple internet technologies engineer, in one of the online presentations that replaced a real-world conference for this year's WWDC.
DOH and DOT also help when you're using a publicly available Wi-Fi network at a place like a hotel or airport, where "your internet usage could be tracked or blocked," he added.

Apple touted its privacy work at its online WWDC event for developers.
With Apple's technique, you'll be able to download encrypted DNS support and add it to an iPhone , iPad or Mac. Once installed, the DNS setting can be modified through the iOS VPN & Network settings or MacOS System Preferences' Network section.
An increasing number of companies offer DNS services. Candidates for support on Apple hardware include companies like Comcast and Cloudflare. Comcast didn't comment for this story, but Cloudflare Chief Technology Officer John Graham Cumming said Apple's move is "fantastic."
He praised Apple for having an app approach that makes encrypted DNS easy to install, works well with companies that might need to control DNS for their own operations, and handles encrypted DNS problems that can crop up when using hotel, airport or coffee shop Wi-Fi. "Encrypted DNS is here to stay. We couldn't be happier," he said.
Apple's approach lets apps other than the browser use encrypted DNS. And it should sidestep some objections DOH critics have had about DOH settings -- for example, that enabling it by default could send people's browsing activity data to companies they know nothing about.
Google added DOT support to Android Pie in 2018, letting you select an encrypted DNS provider like Cloudflare .
Computing Guides
- Best Laptop
- Best Chromebook
- Best Budget Laptop
- Best Cheap Gaming Laptop
- Best 2-in-1 Laptop
- Best Windows Laptop
- Best Macbook
- Best Gaming Laptop
- Best Macbook Deals
- Best Desktop PC
- Best Gaming PC
- Best Monitor Under 200
- Best Desktop Deals
- Best Monitors
- M2 Mac Mini Review
- Best PC Speakers
- Best Printer
- Best External Hard Drive SSD
- Best USB C Hub Docking Station
- Best Keyboard
- Best Webcams
- Best Laptop Backpack
- Best Camera to Buy
- Best Vlogging Camera
- Best Tripod
- Best Waterproof Camera
- Best Action Camera
- Best Camera Bag and Backpack
- Best E-Ink Tablets
- Best iPad Deals
- Best E-Reader
- Best Tablet
- Best Android Tablet
- Best 3D Printer
- Best Budget 3D Printer
- Best 3D Printing Filament
- Best 3D Printer Deals
- Dell Coupon Codes
- Newegg Promo Codes
- HP Coupon Codes
- Microsoft Coupons
- Anker Coupons
- Logitech Promo Codes
- Western Digital Coupons
- Monoprice Promo Codes
- A4C Coupons

IMAGES
VIDEO
COMMENTS
Help. This isn't directly a Let's Encrypt issue, but I'm hoping this audience can help me resolve it as it's obviously deeply related to SSL certificates. (If this is deemed too off-topic, please accept my apologies and let me know.) On macOS (10.14.6), using Safari (13.1), Safari is telling me that it "can't establish a secure ...
Let's Encrypt is a free, automated, and open certificate authority brought to you by the nonprofit Internet Security Research Group (ISRG).Read all about our nonprofit work this year in our 2023 Annual Report.. 548 Market St, PMB 77519, San Francisco, CA 94104-5401, USA. Send all mail or inquiries to:
Let's Encrypt is a free, automated, and open certificate authority brought to you by the nonprofit Internet Security Research Group (ISRG).Read all about our nonprofit work this year in our 2023 Annual Report.. 548 Market St, PMB 77519, San Francisco, CA 94104-5401, USA. Send all mail or inquiries to:
Let's Encrypt is a free, automated, and open certificate authority brought to you by the nonprofit Internet Security Research Group (ISRG).Read all about our nonprofit work this year in our 2023 Annual Report.. 548 Market St, PMB 77519, San Francisco, CA 94104-5401, USA. Send all mail or inquiries to:
Let's Encrypt is a free, automated, and open certificate authority brought to you by the nonprofit Internet Security Research Group (ISRG).Read all about our nonprofit work this year in our 2023 Annual Report.. 548 Market St, PMB 77519, San Francisco, CA 94104-5401, USA. Send all mail or inquiries to:
Let's Encrypt is a free, automated, and open certificate authority brought to you by the nonprofit Internet Security Research Group (ISRG).Read all about our nonprofit work this year in our 2023 Annual Report.. 548 Market St, PMB 77519, San Francisco, CA 94104-5401, USA. Send all mail or inquiries to:
Let's Encrypt is a joint project of EFF, Mozilla, and many other sponsors. If you manage your web site entirely through a web interface, the easiest approach is for your hosting provider to integrate Let's Encrypt support as a setting you can turn on. Many hosting providers already support Let's Encrypt, and many more add support all the time.
Certificates are issued by trusted organizations, such as VeriSign, Inc. or RSA Security, Inc. When you visit an encrypted website—for example, to do online banking—Safari checks if the site's certificate is legitimate. If it's not, Safari warns you. An encrypted website and Safari work together to encrypt information you exchange with ...
Doesn't matter what browser you try on iOS, it just won't work. Also it doesn't open in Safari when browsed on a Mac machine. Other browsers work fine though (Mac OSX only, not iOS). Here is the server configuration: DigitalOcean + Ubuntu 18.04 + Nginx + PHP 7.3 (Laravel) + Let's Encrypt SSL + HTTP2 activated.
To fix the "Not Secure" warning in Safari, website owners can install a Lets Encrypt certificate. This process is automated and can be done for free using a tool such as Certbot. Once the certificate is installed, the website will be able to establish a secure connection with the user's web browser, and the "Not Secure" warning will no longer ...
An encrypted website and Safari work together to encrypt information you exchange with the site. The key used for the encryption is contained in the site's security certificate. This protects your login information, credit card numbers, addresses and other secure data. If you need to connect to a website that requires a personal certificate ...
This is the current Let's Encrypt Hierarchy as of August 2021. The former certificate R3 (Cross-signed by IdenTrust) has since officially been flagged as retired by Let's Encrypt. At DNSimple, we continued to include this certificate in the default intermediate chain we serve from the HTTPS redirector and our DNSimple app certificate installer.
The server is backed by reverse proxy (nginx). I used letsencrypt-powered certificate in order to make it accessible via HTTPS. It works fine via web interface (not excluding Safari in iOS 15), but fails in iOS app: Although, this app seems to accept certificate of https://bitwarden.com.
Let's Encrypt is a free, automated, and open certificate authority brought to you by the nonprofit Internet Security Research Group (ISRG).Read all about our nonprofit work this year in our 2023 Annual Report.. 548 Market St, PMB 77519, San Francisco, CA 94104-5401, USA. Send all mail or inquiries to:
Safari gets new encryption option for network privacy on iPhones, Macs. Apple's approach lets browsers and other apps, too, use encrypted DNS technology on the company's devices. Apple's Safari ...
0. I've a couple of ASP.net websites hosted on Azure and I've installed Let's Encrypt Cert for them. When accessing one of them, although it has a valid Let's Encrypt certificate, on some customers' machines it syas the connection is not secure. The ceriticate is definietly valid but Chrome,Firefox and Edge all say it's not secure:
Let's Encrypt chain update. Let's Encrypt - one of the certificate authorities (CAs) used by Cloudflare - has announced changes in its chain of trust.. As the IdenTrust cross-sign (DST Root CA X3) expires on September 30, 2024, the self-signed ISRG Root X1 will be the only chain used for RSA certificates issued through Let's Encrypt.. This means that, if visitors to your website or ...
Let's Encrypt has revolutionized the way website owners implement HTTPS by offering free and automated SSL certificates, making secure connections accessible to everyone. This article delves into the technical aspects of Let's Encrypt, explaining how it establishes trust and secures your website. Before diving into Let's Encrypt, it's essential to understand the role of a Certificate Authority ...